【天问】2023年Q2恶意包回顾(一)
/ / 点击 / 阅读耗时 24 分钟2023年第二季度,天问Python供应链威胁监测模块共捕捉到473个恶意包。我们细致地分析这些恶意包,并对其常用的攻击方式及混淆类型进行了归纳总结。其中有两类较为突出的有组织的恶意包发布事件,WhiteSnake和BlackCap Grabber。
天问供应链威胁监测模块是奇安信技术研究星图实验室研发的“天问”软件供应链安全分析平台的子模块,”天问“分析平台对Python、npm等主流的开发生态进行了长期、持续的监测,发现了大量的恶意包和攻击行为。
1. WhiteSnake
我们从4月份开始,监控到了许多包含超长base64字符串的恶意包,而且这些恶意包中的内容基本一致。如下 所示:
testWhitesnake-0.1/setup.py
1 | # You got me :D |
由上述代码可知,攻击者首先判定当前的执行环境,然后再选择运行合适的代码。超长的base64字符串编码一般意味着攻击者将可执行文件直接编码嵌入到了Python文件中。针对windows下的base64编码,我们解码后得到了如下代码:
1 | import os as o |
这段代码中包含了一个可执行文件的字节数据。相关安全厂商也对此次攻击做了分析研判,这些恶意包中嵌入的可执行文件,即为一个最近流行的恶意软件WhiteSnake。
我们通过ILSpy对这个样本进行了反编译,如下图所示,这个代码使用了混淆手段来对抗检测,下面是其设计的解码函数。
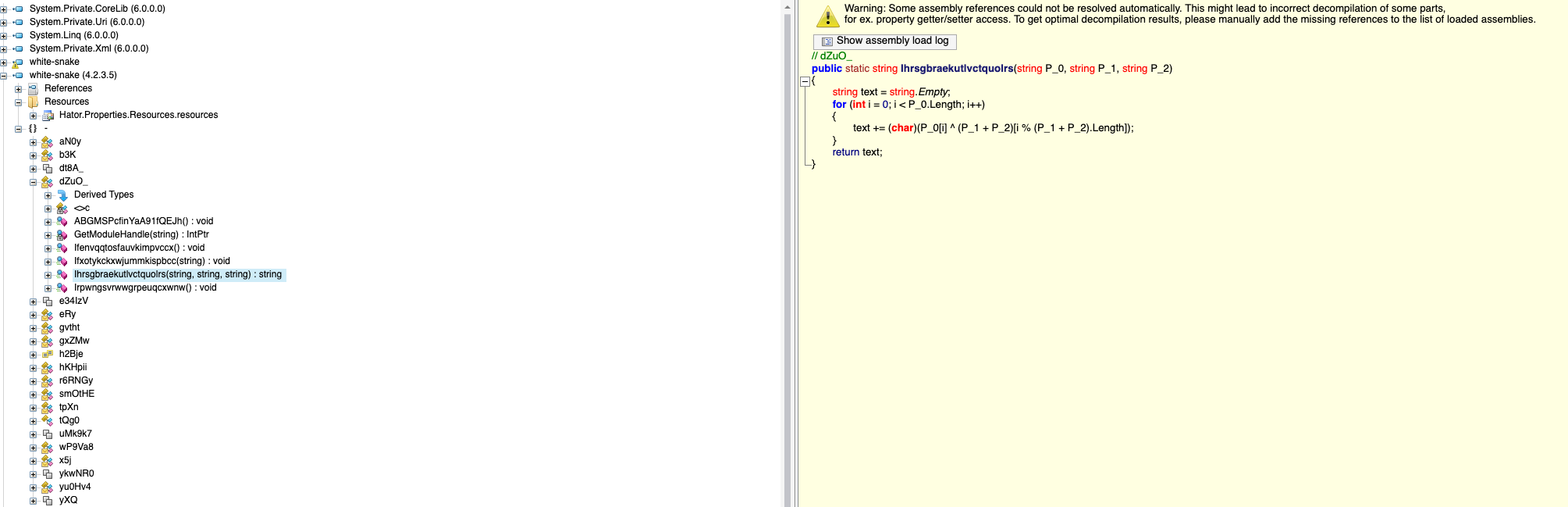
函数解码后,我们可以得到其攻击代码
1 | bool is_admin = new WindowsPrincipal(WindowsIdentity.GetCurrent()).IsInRole(WindowsBuiltInRole.Administrator); |
该程序会在用户主机上添加一个定时任务来执行其恶意程序,并给这个程序赋予最高权限。之后,其会将受害者主机的敏感信息通过私密的Telegram聊天进行回传,包括屏幕截图、用户名、主机名、IP等一系列信息。
由附录中的恶意包列表可知,这些恶意包来自于少数几个PyPI的账户。鉴于这些恶意包内容基本一致,所以我们推断这些账户极有可能是同一个组织或个人创造的。我们也会对这些账户及相应的恶意包进行持续性监控。
2. BlackCap Grabber
在2023年Q2的监控中,我们发现了大量包含相同内容的恶意包。其内容如下所示:
piptyper-1.0.0/__init__.py
1 | import requests |
经过分析查找,我们确认了这些恶意包的源码来自GitHub中一个开源项目token-grabber。项目介绍表明这是一个Token窃取和捕获工具,可以窃取discord密码,信用卡信息等各种敏感数据。
从上面的代码中,我们可以看到攻击者最开始会用httpx.post回传受害者的主机名到一个特定的网址,而且这个网址在后续代码中的配置信息中也出现了。yourwebhookurl: "https://kekwltd.ru/relay"。我们依据这个信息,找到上述恶意包对应的webhookurl,共有8种。这些webhookurl和包名的对应关系如下所示:
| webhookurl | 包名 |
|---|---|
| https[:]//realbatman.com/ | pyfontslibv2-0.1.0,pylibfonts-0.1.0,pylibfont-0.1.0,pyfontstyle-0.1.0,pylibsql-0.1.0,pylibsqlite-0.1.0 |
| https[:]//vkiod3bec0gmmc4yspoaqu.hooks.webhookrelay.com/ | randgenlib-1.0.2 |
| https[:]//k8c7nxg6riaq9nueln6wjd.hooks.webhookrelay.com/ | pik-utils-1.0.2,requestlib-1.0.2,totohateinenkleinencock-1.0.0,py-obfuscater-1.0.2 |
| https[:]//ptb.discord.com/api/webhooks/110305598327569 2132/e7l2YWNN0tBr7Vbx_UliNYnKNo0G3_SeBsNAVO3bCM e7Mo0y89bTgRK6j2dR5DpQ0Tau |
pythoncryptlibery-1.0 |
| https[:]//prepaidroot.ru/relay/ | pycryptlibraryv3-0.6 |
| https[:]//kekwltd.ru/relay/ | piphelperlib-1.0.0等79个包 |
| https[:]//kekwltd.ru/relay/bluescreen | pythoncolorv4-1.0.0等17个包 |
| https[:]//bananasquad.ru/handler | pipcolourextension-1.1.0等6个6月份发布的恶意包 |
从这些webhookurl的分布,我们可以推断多数恶意包来自同一个组织或个人,这些组织之间是否存在关联尚不清楚。6月份发现的相关包使用了fernet做了一层混淆,而且webhookurl的地址也发生了改变,经测试之前顶级域名为.ru结尾的url已经失效,且被标记为了钓鱼网站。
目前,此类恶意包事件还在PyPI中零星发生,这些恶意包通常以py,lib,crypto此类单词来伪装自己,用户需要警惕。我们也会持续关注此类攻击事件,并及时发布相关报告。
3. 恶意包案例分析
在2023年Q2的监控中,我们发现了一个精心设计的恶意包easyrequests-1.0.0,其利用了多种方式来隐藏自己的攻击行为。
首先,这个恶意包将base64编码后的攻击代码隐藏在了setup.py中,其借助代码编辑器显示宽度的限制来进行了隐藏,如下图所示。
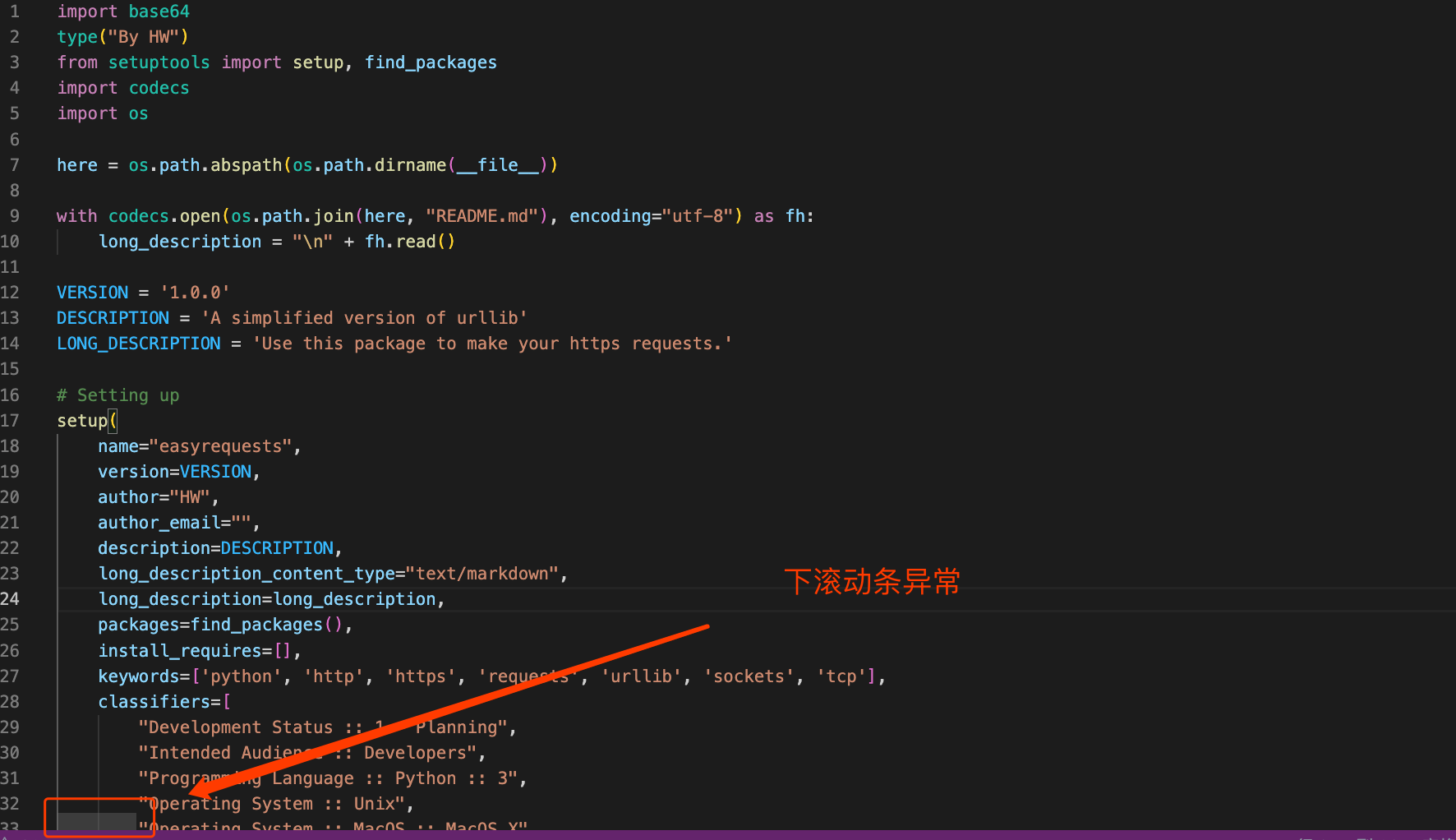
easyrequests-1.0.0/setup.py
1 | import base64 |
base64代码解码处理后如下所示
1 | import os |
这段代码会从https[:]//api-hw.com/dl/runtime下载runtime.zip,其提供了完整的代码执行环境,部分内容如下图所示。
其执行了其中的stub.pyw,.pyw文件执行时会保持静默,不会弹出命令行窗口
stub.pyw
1 | wopvEaTEcopFEavc ="FW@C}ReuWWBrtUNR\x15\r\x16oh..." |
观察代码可知,混淆代码利用了按位异或的方式。输出最后compile(oIoeaTEAcvpae, '<string>', 'exec'))代码的执行结果,可得到如下代码
1 | wopvEaTEcopFEavc ="YYHZBA\x13^BVW8ZT..." |
这个混淆方式与上面的相同,但执行compile(oIoeaTEAcvpae, '<string>', 'exec')得到的是一个代码对象,我们通过第三方库dis得到了其汇编代码,部分汇编代码如下所示
1 | 292 LOAD_NAME 9 (requests) |
完整的汇编代码中会窃取用户主机上的隐私信息,例如chrome的密码等,然后回传到上面汇编代码中的两个url。
这个攻击样本经过精心设计,包名easyrequests模仿了流行包requests,而其攻击源代码经过了编译以及多种混淆方式的处理,其中还包括了自定义的按位异或混淆处理。其下载的文件提供了完整的执行环境和依赖文件,由此推测这是一次目的性很强的针对性攻击,而且攻击者对于Python的各种特性较为了解。目前相关恶意包已被删除,我们也会持续关注PyPI中这类恶意包的相关事件。
4. 结语
从2023年Q2的恶意包分析中,我们可以看到目前PyPI中的恶意攻击开始呈现大规模,组织化的趋势。WhiteSnake和BlackCap Grabber事件表明攻击者利用的工具越来越丰富,无论是付费的恶意软件还是开源代码都开始被攻击者植入恶意包中。这些软件和代码的针对性更强,危害也更大,用户需要加强警惕,不轻易下载未知包。我们也会持续关注PyPI中恶意包的相关动向,并及时发布相关报告。
5. 附录(恶意包列表)
恶意包列表
WhiteSnake
包名 上传日期 作者 test24234-0.4 04-14 MyTestAccount1 test24234-0.1 04-14 MyTestAccount1 test23414234234-0.6 04-14 MyTestAccount1 test-23234231-0.1 04-14 MyTestAccount1 test-23234231-10 04-14 MyTestAccount1 test-23234231-0.9 04-14 MyTestAccount1 test-23234231-11 04-14 MyTestAccount1 testWhitesnake-0.1 04-14 MyTestAccount1 testWhitesnakeModule-0.1 04-14 MyTestAccount1 aeodatav04-0.4 04-14 erotic1 aeodata-0.4 04-14 erotic1 aietelegram-0.3 04-21 erotic1 qsteemp-0.2 04-22 erotic1 qsteemp-0.5 04-22 erotic1 setnetwork-0.2 04-27 erotic1 setnetwork-0.3 04-27 erotic1 aeivasta-0.3 04-20 santic12 Scrappers-dev-4.1 04-21 develepor_pyton_telethon detection-telegram-5.6 04-21 develepor_pyton_telethon parser-scrapper-7.2 04-22 develepor_pyton_telethon androidspyeye-2.5 04-17 develepor_pyton_telethon support-dev-7.8 04-17 develepor_pyton_telethon support-hub-0.8 04-18 develepor_pyton_telethon social-checker-7.2 04-19 develepor_pyton_telethon Scrappers-3.5 04-20 develepor_pyton_telethon quick-telegram-sender-0.7 04-25 develepor_pyton_telethon social-scrapper-3.6 04-25 develepor_pyton_telethon tg-bulk-sender-2.3 04-28 develepor_pyton_telethon social-scrappers-2.3 04-28 develepor_pyton_telethon tiktok-phone-cheker-2.42 04-28 develepor_pyton_telethon pandirequests-0.1 04-22 Brazil panderequests-0.1 04-22 Brazil panderequests-0.2 04-22 Brazil libidrequest-0.4 04-23 Brazil libidreq-0.1 04-27 Brazil libide-0.1 04-29 Brazil pandarequest-0.1 04-23 Portugal cloudfix-1 04-29 LecheEnjoyer420 cloudfix-1.34 04-29 LecheEnjoyer420 cloudfix-2 04-29 LecheEnjoyer420 cloudfix-0.0.0 04-29 LecheEnjoyer420 Networkfix-2 04-29 JSmith420 libid-0.1 05-01 Brazil testfiwldsd21233s-0.1 05-02 trnhso2312 setdotwork-0.6 05-03 erotic1 setdotwork-0.7 05-03 erotic1 webtraste-0.3 05-04 erotic1 libidos-0.1 05-05 Portugal libidi-0.1 05-06 Brazil lindze-0.1 05-06 Portugal colorara-0.1 05-07 Brazil libida-0.2 05-07 Portugal sobit_ishlar-0.1 05-09 develepor_pyton_telethon BootcampSystem-0.1 05-09 contadaica1 tryconf-0.1 05-11 develepor_pyton_telethon tryhackme_offensive-0.4 05-12 develepor_pyton_telethon libig-0.1 05-13 Brazil libidee-0.1 05-13 Brazil libideee-0.1 05-13 Brazil libideeee-0.1 05-13 Brazil myshit12223-1.0 05-27 asdaweadssadf myshit12223-2.0 05-27 asdaweadssadf multitools-0.1 05-29 erotic1 multitools-0.2 05-29 erotic1 multitools-0.3 05-29 erotic1 libiobe-0.1 06-06 Portugal eth-keccak-0.1 06-21 shuser777 bignum-devel-1.5.2 06-22 andrewfufu uniswap-math-0.4.2 06-23 chbraver sql-to-sqlite-1.2 06-23 chbraver pysqlchiper-conv-0.4.7 06-23 chbraver pysqlcipher-conv-0.4.7 06-23 chbraver BlackCap Grabber
包名 上传日期 作者 piphelperlib-1.0.0 04-03 Jakob_Horn piptyper-1.0.0 04-03 bussardweg4a pylibhelper-1.0.0 04-03 jakobhornbussardweg4a CryptoUtilities-1.0.0 04-03 RonnieMcNutt1243 pypackagehelp-1.0.0 04-04 bussardweg4aontop pycryptlib-1.1.5 04-08 beinpresse160kg piplibaryscrape-1.2.0 04-10 skrrbrrskrrbrr pycryptolibrary-2.0.0 04-11 pypiuser583 pylibcrypto-1.2.0 04-11 pypiuser924 pyaescrypter-1.0.0 04-11 NagelNeuerBenza piplibcrypto-1.2.0 04-12 beinpresse101kg pylibcrypt-1.3.1 04-12 beinpresse100kg pycryptography-3.0.0 04-12 beinpresse104kg pycryptographier-1.8.7 04-12 beinpresse105kg cryptographylib-1.2.0 04-12 beinpresse106kg cryptolibs-1.2.0 04-12 beinpresse107kg piplibcrypter-1.1.0 04-14 beinpresse110kg pipcryptographylibaryV2-1.2.0 04-14 beinpresse103kg randgenlib-1.0.2 04-14 randpwgen tommygtst-0.1.0 04-14 getynow pycryptlibraryv3-0.6 04-15 uhesjgnesgk pipcolorlibraryV1-1.0.0 04-16 RonnieMcNutt54353 testdontdownloadthis-1.0.0 04-17 pypitester187 testdontdownloadthis-1.0.1 04-17 pypitester187 pipcryptliberyV2-1.1.0 04-17 beinpresse101kg pythoncoloringslibV2-2.0.0 04-18 beinpresse103kg requestlib-1.0.2 04-19 smallalex totohateinenkleinencock-1.0.0 04-19 nigaalex pipcolourlibV1-1.0.0 04-20 Ab7KannManSchieben pythoncryptlibaryV2-1.0.0 04-20 RonnieMcNutt1243 pycryptolibV2-1.0.0 04-20 RonnieMcNutt1243 pythoncolouringslibV1-1.0.0 04-21 RonnieMcNutt1243 pipcryptographylibraryV2-1.2.0 04-21 beinpresse108kg pipcryptographylibV1-2.0.0 04-22 beinpresse109kg pipcolouringslibV1-1.5.1 04-22 beinpresse105kg pyfontslib-1.0.0 04-23 RonnieLeon564 pik-utils-1.0.2 04-23 Kennethi723 pythoncolouringliberyV1-1.0.0 04-24 Beinpresse200kg pycryptolibary-1.0.0 04-24 RonnieMcNutt1243 pyfontslibrary-1.0.0 04-25 SchwarzerRitter187 pipcolorlibV3-1.0.0 04-25 RonnieMcNutt1243 pipcoloringlibary-1.0.0 04-26 RonnieMcNutt1243 pyfontslibraryV1-1.2.0 04-26 beinpresse105kg pythoncolourlibraryV1-1.0.0 04-27 Josephb536 pipcoloringliberyV2-1.0.0 04-27 RonnieMcNutt1243 pyfontslibv2-0.1.0 04-29 Andreasfrr pipcryptov4-1.0.0 05-01 RonnieMcNutt1243 pythoncolorv4-1.0.0 05-01 RonnieMcNutt1243 pythoncolourv8-1.0.0 05-01 RonnieMcNutt1243 pythoncryptov4-1.0.0 05-01 RonnieMcNutt1243 syssqlitemods-1.0.0 05-01 ohwivfznmnrueqk syscoloringspkg-1.0.0 05-01 txybrpiwipkzmkl syssqlite2toolsV2-1.0.0 05-01 drbnebolxdutltm pythoncolorlibV1-1.0.0 05-01 owcfdzhhmqwgjgw syscryptographymodsV2-1.0.0 05-01 lxjbpqieywlsuka pycolourkits-1.0.0 05-01 ueywzmolqdhfirj pythonsqlite2toolsV1-1.0.0 05-01 yfybcyxuhyzjdom pythoncryptolibV2-1.0.0 05-01 hgfclsceuqhvdba pythonfontingaddonV1-1.0.0 05-01 ycftvyjekyjzjag pipcoloringsextV1-1.0.0 05-01 mvnwgoszgjlhvua pythoncryptoaddition-1.0.0 05-01 zselohpbtzpirxc pipfontingaddonsV2-1.0.0 05-01 qobtkkdbxpishke pipsqlpackageV2-1.0.0 05-01 zkwdwqymyegshke pycoloringpkgsV2-1.0.0 05-01 cpepnswoderaoaf pyfontstyle-0.1.0 05-01 Andreasfrr pythonsqlitetool-1.0.0 05-01 mvnwgoszgjlhvua pythonsqlite2mod-1.0.0 05-02 hgyywhaitgjptld pylibfont-0.1.0 05-02 Andreasfrr pipsqlitedblibrary-1.0.0 05-02 wpfeyhchukhxrfe pylibfonts-0.1.0 05-02 Andreasfrr pipcolourpackagesV2-1.0.0 05-02 tkbgkknemiotxuj syssqlite2package-1.0.0 05-02 bzyweegutqitvbq syscryptolibV1-1.0.0 05-02 gdfjceyrzdlkznm syscryptlibV2-1.0.0 05-02 txybrpiwipkzmkl pysqlilibraryV1-1.0.0 05-02 zkwdwqymyegshke sysdatalib-0.0.2 05-02 jan-karam pylibsql-0.1.0 05-02 Brrrrraaaaa pipcryptaddsV2-1.0.0 05-02 qobtkkdbxpishke pythoncryptlibery-1.0 05-02 johnbanks1234 pylibsqlite-0.1.0 05-02 Brrrrraaaaa pysqlite3pkgV2-1.0.0 05-02 irfddryprjkploh pyapicolorv2-0.0.1 05-02 jan-karam pythoncolouringslibV2-1.0.0 05-02 pypiuser583 pythoncolouringslibV2-2.1.1 05-02 pypiuser583 syscolourtoolkit-1.0.0 05-03 txybrpiwipkzmkl syssqlite3V2-1.0.0 05-03 vdjhyjdvpddeeuy pyfontinglib-1.0.0 05-03 Bluescreen36 pycolouringlibrary-1.0.0 05-04 RonnieMcNutt1243 pipcolorv2-1.0.0 05-05 RonnieMcNutt1243 py-obfuscater-1.0.2 05-06 Vector_Dev pipcolouringv1-1.0.0 05-07 RonnieMcNutt1243 pythoncolourliberyV2-1.0.0 05-07 RonnieMcNutt1243 pipcryptov2-1.0.0 05-07 RonnieMcNutt1243 pipcryptov2-1.0.0 05-07 RonnieMcNutt1243 colopym2-0.0.1 05-07 jan-karam pythonfontsv2-1.0.0 05-08 RonnieMcNutt1243 pycolorv3-1.0.0 05-09 RonnieMcNutt1243 pipcolouraddonsV1-1.1.0 05-12 beinpresse106kg syscryptpackageV1-1.1.0 05-12 beinpresse105kg pysqlite3addonV1-1.1.0 05-12 beinpresse104kg pipsqlite3liberyV2-1.1.0 05-13 beinpresse101kg pythonsqlite2additionV1-1.1.0 05-13 beinpresse103kg pythoncolouringpkgV1-1.1.0 05-13 beinpresse107kg pycoloringextV1-1.1.0 05-13 beinpresse110kg pycoloringextV1-1.1.0 05-13 beinpresse110kg pipfontingv2-1.0.0 05-15 PythonCoder152 pythonfontingv2-1.0.0 05-15 RonnieMcNutt1243 pythoncoloringv1-1.0.0 05-16 RonnieMcNutt1243 pipfontingv1-1.0.0 05-16 RonnieMcNutt1243 pipcolourextension-1.1.0 06-22 pzdmfplmldxwrsh syscoloringspkgs-1.1.0 06-22 tpfrarrvplanumb syssqliteaddV2-1.1.0 06-23 pzdmfplmldxwrsh syssqlite2toolV2-1.1.0 06-23 hsfmsnavcgykfqh pythoncryptographypackage-1.1.0 06-23 acgwtcjrvrztead syscryptographymodsV1-1.1.0 06-26 kristiepatton520 混淆样本
包名 上传日期 作者 easyrequests-1.0.0 05-12 https-requester dfdfdfdfhhh-1.0.0 05-12 hhhgggfgff pybowl-1.0.0 05-12 hhhgggfgff pybowl-1.0.4 05-12 hhhgggfgff